Click Fraud - How to Detect & Prevent
Everything in this article:
- What is Click Fraud?
- How is Click Fraud done?
- Headless Chrome Servers
- Botnets
- Cheap human labor
- Detecting Click Fraud
- Detecting Click Fraud by IP address
- Tor Exit Nodes & Click Fraud
- Preventing Click Fraud with Captcha
- Preventing Click Fraud with ReCaptcha
- Preventing Click Fraud with Cloudflare
- Click fraud on Google Ads
- The Final Word on Click Fraud Protection & Mitigation
What is click fraud?
Click fraud is the process of clicking on adverts with clicks that are not real customers, hence artificially inflating the amount an advertiser pays.
There is a lot of click fraud on the internet, even on large platforms such as Google Ads and Facebook.
Historically, ad platforms have been slow to act, as unfortunately they unintentionally benefit from click fraud.
How Click Fraud is Done
Headless Chrome Servers
A headless browser is a web browser that has been designed to be operated in an automated fashion, with robots clicking on links and ads.
Usually these are ‘headless chrome’ browsers that run on servers in data centers.
These tend to be easy to detect as datacenters have well known IP addresses.
Botnets
These are normal people’s computers that have been infected with malware that run headless browsers in the background.
In these circumstances, people are typically unaware that their computer has been hijacked.
These are tougher to detect, as the IP address is that of what would otherwise be a legitimate user’s computer.
Cheap Human Labor
In what amounts to organized crime online, we see cheap human labor being used to browse and click on ads.
Astonishingly, click fraud has become a major business for organized crime, with some reports suggesting it tallies just behind the drug trade.
Detecting Click Fraud
The obvious indicator of click fraud is low conversion rate, but this can be difficult to pick out when multiple streams of traffic are blended together on a website.
Detecting Click Fraud by IP Address
An IP address is a 12-digit number that references a particular computer on the internet.
IP addresses are provided to computers by the computer's internet service provider (ISP).
The most common click fraud is performed with headless chrome robots running on servers.
These are normally easy to detect, as they commonly use cloud internet service providers, such as Amazon Web Services, Azure or Google Cloud.
The IP addresses of the 'clickers' can be looked up in public directories of IP addresses which indicate which internet service provider the IP address belongs to.
Traffic coming from a cloud provider is almost always non-human traffic.
Tor Exit Nodes & Click Fraud
Tor, otherwise known as the anonymous internet, is a global anonymizer service that makes it difficult (if not impossible) to determine who is requesting a web page.
People may use Tor for legitimate privacy reasons, but typically, these aren’t customers.
Helpfully, the Tor Project publishes a list of Tor Exit Nodes.
These nodes are the IP addresses that belong to Tor, and visitors will appear to have one of these IP addresses.
It is fair to assume that any clicks originating from Tor will be unlikely to convert, and may be fraudulent.
Detecting Click Fraud with Timestamps
Another way is to see how quickly things are being clicked.
There’s normally a significant delay between a human’s first and second click, whereas most click fraud robots are not as sophisticated.
In this scenario, we might see a visitor click an element on the page right after it has loaded, rather than waiting the few seconds that a human would take to read the page.
Preventing Click Fraud with Captcha
Captcha (Completely Automated Public Turing test to tell Computers and Humans Apart) are the challenges we’ve all seen online to help prevent bots.
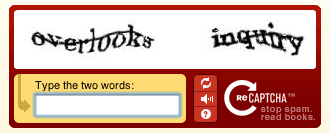
In short, these old-fashioned captchas are no longer effective at all, and also degrade the user experience.
They are normally easily beaten by captcha solving services, which utilise free or cheap labour to solve these in realtime on behalf of spammers and fraudsters.
Preventing Click Fraud with ReCaptcha
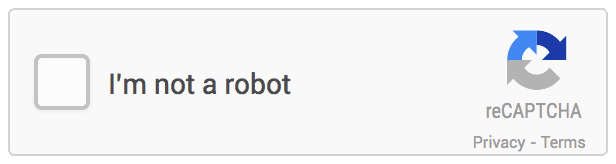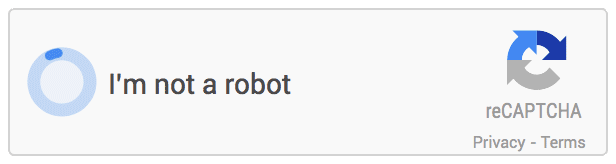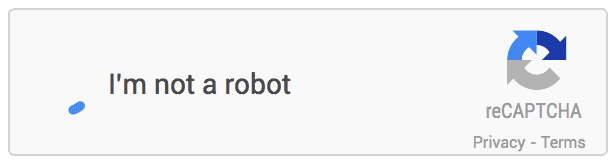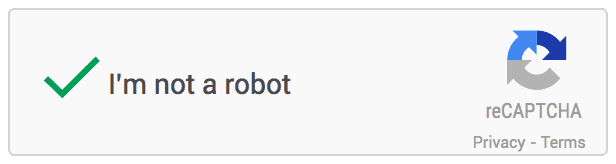
ReCaptcha is Google’s implementation of Captcha. There have been three versions, of which v2 and v3 are currently supported.
Google’s ReCaptcha v2 is the one that asks users to click on items in a photograph:

Google’s ReCaptcha v3, however, is completely invisible. It works by profiling the browser, IP address, and behaviour of users.
It is remarkably effective, and as it is invisible, produces a seamless user experience.
Google ReCaptcha v3 works well thanks to Google's huge reach on the internet.
It can see the behaviour of individual IP addresses across websites, and consequently can build a much better profile of the nature of the activity by that IP.
Google ReCaptcha v3 returns a score between 0 and 1, with 1 being very likely human, and 0 being almost certainly automated. Most scores are either 0.1 or 0.9, with little in between, suggesting Google ReCaptcha v3 can discern traffic with little uncertainty:
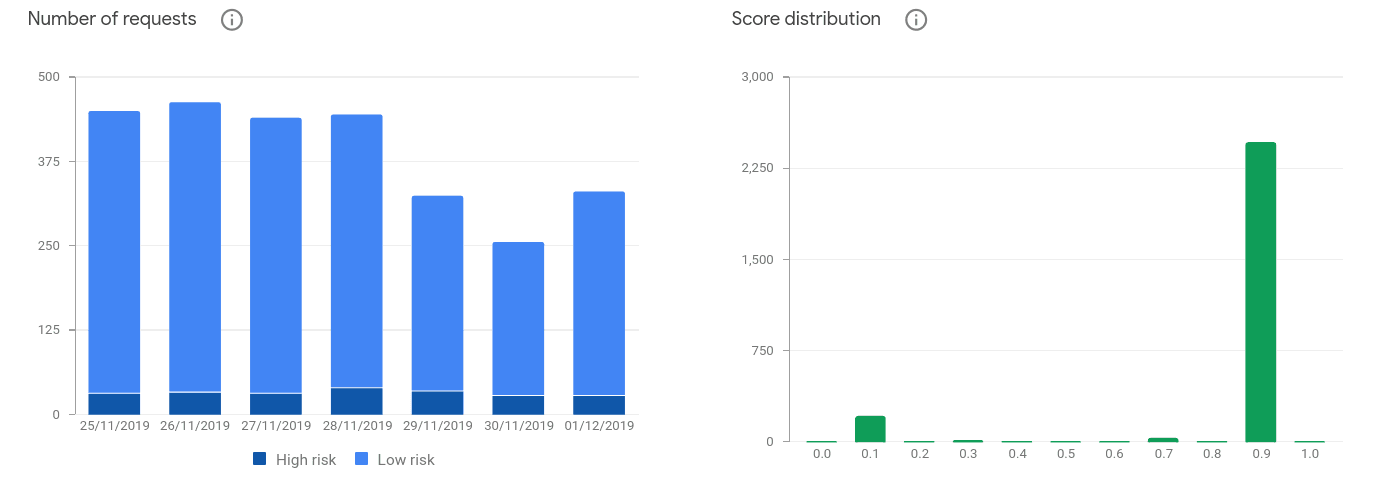
Google ReCaptcha v3 has an Admin dashboard, which allows you to see the distribution of traffic and its score. Numbers greater than 0.5 indicate likely human, whereas numbers closer to 0 indicate likely bots or other abusive traffic.
Google ReCaptcha v3 really is the gold standard of online click fraud protection.
Google Recaptcha v3 is integrated with Linkly, and forms the core of Linkly’s click fraud protection.
Notable Mention — Preventing Click Fraud with Cloudflare
Cloudflare, the world’s largest DNS and CDN provider, has an enterprise product for bot detection:
Unlike Google's ReCaptcha, which runs in the user's browser, this works by inserting Cloudflare as a proxy between your website and the user.
Cloudflare, thanks to being one of the internet’s largest edge providers, can see which users exhibit bot-like behaviour, and flag them accordingly.
Like ReCaptcha, Cloudflare’s bot protection provides a score, which is provided alongside the request for a page from your site.
Unlike ReCaptcha, however, Cloudflare’s bot protection & mitigation service is currently an enterprise only product.
Click Fraud & Google Ads
**Click fraud happens with Google Ads. **
Anecdotally, some say as much as 20% of the traffic purchased from Google is fraudulent.
It might be a competitor trying to waste your budget, or a publisher clicking on on-site ads to inflate their Adsense revenues.
It happens so much that an entire industry has been set up around trying to mitigate click fraud specifically from Google Ads.
Companies such as Clixtell, ClickCease, and ClickGuardian (amongst perhaps 20 more) exist solely to try and flag click fraud from Google.
Google defines exactly what it considers to be invalid clicks, and has an entire process for requesting a refund. In the latter case, you’ll need to provide clear evidence of click fraud.
The issue with using these services is that they rely on overly simplistic methods of detecting click fraud.
Generally speaking, using Linkly’s ReCaptcha V3 Click Fraud Protection is an effective solution here, and has the added advantage that it has a free plan.
The Final Word on Click Fraud Protection & Mitigation
It's incredibly difficult to catch all forms of click fraud and other abusive behaviour online.
There are financial incentives for fraudsters and ad networks, with the advertiser being left to foot the bill.
Using tools like Cloudflare or ReCaptcha, or Linkly’s own ReCaptcha integration, can help reduce click fraud overall.

